Salesforce-MuleSoft-Platform-Integration-Architect Practice Test
Updated On 1-Jan-2026
273 Questions
A banking company is developing a new set of APIs for its online business. One of the
critical API's is a master lookup API which is a system API. This master lookup API uses
persistent object store. This API will be used by all other APIs to provide master lookup
data.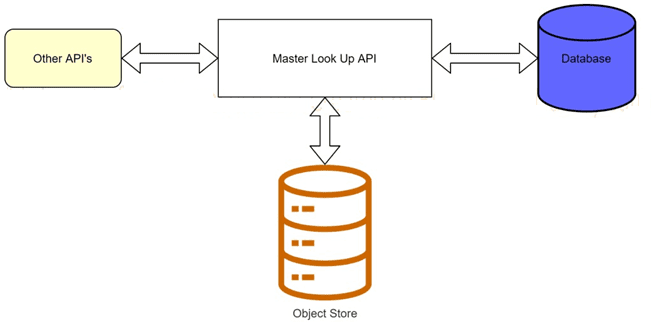
Master lookup API is deployed on two cloudhub workers of 0.1 vCore each because there
is a lot of master data to be cached. Master lookup data is stored as a key value pair. The
cache gets refreshed if they key is not found in the cache.
Doing performance testing it was observed that the Master lookup API has a higher
response time due to database queries execution to fetch the master lookup data.
Due to this performance issue, go-live of the online business is on hold which could cause
potential financial loss to Bank.
As an integration architect, which of the below option you would suggest to resolve
performance issue?
A. Implement HTTP caching policy for all GET endpoints for the master lookup API and implement locking to synchronize access to object store
B. Upgrade vCore size from 0.1 vCore to 0,2 vCore
C. Implement HTTP caching policy for all GET endpoints for master lookup API
D. Add an additional Cloudhub worker to provide additional capacity
Explanation
The root cause of the performance issue is clearly stated: "higher response time due to database queries execution to fetch the master lookup data." The solution must address this specific bottleneck.
Why C is Correct (HTTP Caching Policy):
An HTTP Caching Policy in API Manager is applied at the gateway level. When a request is made to the Master Lookup API, the policy can be configured to store the API's response.
Subsequent identical requests for the same data will not even reach the Mule application. They are served directly from the cache at the gateway layer, resulting in a massive reduction in response time.
This directly eliminates the need for the Mule application to execute the logic to check the Object Store and, more importantly, prevents the expensive database query for the lifetime of the cached item. This is the most effective way to solve the stated problem.
Why the Other Options Are Incorrect or Less Effective:
A. Implement HTTP caching policy... and implement locking to synchronize access to object store:
The first part (HTTP Caching) is correct. However, the second part (implementing locking) is unnecessary and would likely degrade performance further.
The Object Store is already thread-safe and cluster-aware. Manually adding locking mechanisms would introduce contention and complexity without solving the core issue, which is the database call.
B. Upgrade vCore size from 0.1 vCore to 0.2 vCore:
While a larger vCore provides more CPU, the bottleneck is not CPU processing power; it's the I/O wait time spent on the database query. Throwing more CPU at an I/O-bound problem provides minimal benefit and is a cost-ineffective solution. The database will remain the bottleneck.
D. Add an additional Cloudhub worker to provide additional capacity:
Adding more workers helps with throughput (handling more concurrent requests) but does not improve the latency (response time) of an individual request.
Each request, regardless of which worker handles it, will still be slow because it will still need to query the database. This "scaling out" approach does not fix the fundamental performance flaw in a single request's path.
Architectural Analysis
The proposed solution (C) creates a highly efficient architecture:
First Request:
Misses the cache, goes to the Mule app, which checks its Object Store, misses, queries the database, stores the result in the Object Store, and returns the response. The HTTP Caching policy stores this response.
Subsequent N Requests:
For the cached time-to-live (TTL), the request is served instantly from the API Manager cache. The Mule application and database are completely bypassed, providing the fastest possible response.
Key References
MuleSoft Documentation: HTTP Caching Policy
This policy is designed explicitly for this use case: to reduce latency and backend load by caching responses.
Link: HTTP Caching Policy
In summary, the most direct, effective, and cost-efficient solution to eliminate database-induced latency is to implement an HTTP Caching Policy, which serves repeated requests directly from the gateway cache.
A system administrator needs to determine when permissions were last changed for an Anypoint Platform user. Which Anypoint Platform component should the administrator use to obtain this information?
A. Audit Logging
B. Anypoint Monitoring
C. Anypiont Studio
D. Mule Stack Traces
Explanation
The requirement is to track a change in permissions for a user, which is a security and administrative event. Anypoint Platform's Audit Logging is specifically designed for this purpose.
Why A is Correct (Audit Logging):
The Audit Log is a comprehensive record of security-sensitive and administrative actions performed within an Anypoint Platform organization and its business groups.
It captures events such as user logins, permission changes, role assignments, API policy changes, and application deployments.
An administrator can query the audit log to find entries related to a specific user and filter for events like "User Updated" or "Role Assigned" to see exactly when their permissions were modified and by whom.
Why the Other Options are Incorrect:
B. Anypoint Monitoring:
This component is used for tracking the performance and health of Mule applications and runtimes. It provides metrics like CPU usage, memory, throughput, and latency. It does not track administrative or security events like user permission changes.
C. Anypoint Studio:
This is the integrated development environment (IDE) for building Mule applications. It has no functionality for auditing user permissions or administrative actions on the Anypoint Platform.
D. Mule Stack Traces:
These are generated when a Mule application encounters a runtime error. They are used by developers to debug application logic and are unrelated to platform-level user management and auditing.
Key References
MuleSoft Documentation: Audit Logging
This is the definitive source that lists the types of events logged, which include user and permission management activities.
Link: Anypoint Platform Audit Logging
In summary, when an administrator needs to investigate who did what, when, and to whom on the Anypoint Platform itself, the Audit Log is the correct and only component to use.
An organization is sizing an Anypoint VPC for the non-production deployments of those
Mule applications that connect to the organization's on-premises systems. This applies to
approx. 60 Mule applications. Each application is deployed to two CloudHub i workers. The
organization currently has three non-production environments (DEV, SIT and UAT) that
share this VPC. The AWS region of the VPC has two AZs.
The organization has a very mature DevOps approach which automatically progresses
each application through all non-production environments before automatically deploying to
production. This process results in several Mule application deployments per hour, using
CloudHub's normal zero-downtime deployment feature.
What is a CIDR block for this VPC that results in the smallest usable private IP address
range?
A. 10.0.0.0/26 (64 IPS)
B. 10.0.0.0/25 (128 IPs)
C. 10.0.0.0/24 (256 IPs)
D. 10.0.0.0/22 (1024 IPs)
Explanation
The requirement is twofold:
Hide sensitive values from being stored or visible in cleartext in Runtime Manager.
Allow Administrators to change these values within Runtime Manager.
The mechanism designed specifically for this in Mule 4 is the Secure Properties feature, which is configured in the mule-artifact.json file.
Why A is Correct (mule-artifact.json):
The mule-artifact.json file contains metadata about the Mule application. It includes a secureProperties section where you declare the names of the properties that are considered sensitive (e.g., ["db.password", "api.client.secret"]).
How it works:
During deployment (via CI/CD), you do not provide the values for these properties in the properties section of the deployment command/UI.
Because the properties are listed in secureProperties, Runtime Manager treats them as secure.
After the application is deployed, a Runtime Manager Administrator can navigate to the application in the UI, go to the Properties tab, and input the actual values for these properties. The values are stored encrypted and are never displayed in cleartext.
This perfectly satisfies the requirement:
the values are not stored in cleartext in the CI/CD pipeline or visible in Runtime Manager, yet authorized admins can change them directly in Runtime Manager.
Why the Other Options are Incorrect:
B. Add encrypted versions of the sensitive properties as global configuration properties:
This is incorrect and insecure. If you encrypt the properties within the application itself, you must store the decryption key somewhere, leading to a circular problem. Furthermore, this approach does not allow administrators to change the values in Runtime Manager; it would require a code change and redeployment.
C. Add a new wrapper.java.additional.xx parameter in the wrapper.conf file:
The wrapper.conf file is part of the Mule runtime and is used to set JVM arguments. This is not the mechanism for application-level properties in CloudHub. CloudHub does not give you direct access to modify the wrapper.conf file for a worker, and this approach would not integrate with Runtime Manager's property management interface for administrators.
D. Create a variable for each sensitive property and declare them as hidden in the CI/CD pipeline scripts:
Hiding a variable in a CI/CD script (e.g., as a secret variable in Jenkins or Azure DevOps) only protects it within the pipeline. When the deployment command is executed, the value would still be passed as a cleartext property to Runtime Manager, making it visible there and violating the core requirement.
Key References
MuleSoft Documentation: Secure Properties in Runtime Manager
This is the definitive guide on how to configure properties as secure in the mule-artifact.json file.
In summary, the only correct and MuleSoft-supported method to hide sensitive properties from CI/CD and the Runtime Manager UI, while still allowing admins to set them post-deployment, is to declare their names in the secureProperties array within the application's mule-artifact.json file.
A new Mule application has been deployed through Runtime Manager to CloudHub 1.0
using a CI/CD pipeline with sensitive properties set as cleartext. The Runtime Manager
Administrator opened a high priority incident ticket about this violation of their security
requirements indicating
these sensitive properties values must not be stored or visible in Runtime Manager but
should be changeable in Runtime Manager by Administrators with proper permissions.
How can the Mule application be deployed while safely hiding the sensitive properties?
A. Add an ArrayList of all the sensitive properties’ names in the mule-artifact.json file of the application
B. Add encrypted versions of the sensitive properties as global configuration properties in the Mule application
C. Add a new wrapper.java.additional.xx parameter for each sensitive property in the wrapper.conf file used by the CI/CD pipeline scripts
D. Create a variable for each sensitive property and declare them as hidden in the CI/CD pipeline scripts
Explanation
The requirement has two key parts:
Hide from Runtime Manager:
The sensitive values must not be stored or visible in cleartext within the Runtime Manager UI.
Changeable by Admins:
Authorized administrators must still be able to change these values through Runtime Manager.
Let's analyze why the Secure Properties feature is the only one that meets both requirements.
Why B is Correct (Secure Properties):
How it works:
In your Mule application's mule-artifact.json file, you can declare certain properties as "secure" by adding their keys to the secureProperties array.
Deployment:
When you deploy the application (e.g., via CI/CD), you do not provide the cleartext value. Instead, you deploy the application with the property key present but its value empty or as a placeholder.
Post-Deployment Configuration:
After deployment, an authorized Runtime Manager administrator logs into the UI, navigates to the application's properties, and sets the actual sensitive value. Runtime Manager encrypts and stores this value at rest, and it is never displayed in the UI again (only masked with asterisks).
Runtime:
The Mule runtime securely fetches and decrypts the value when needed. This perfectly satisfies both security and operational requirements.
Why A is Incorrect:
Simply listing the property names in mule-artifact.json is only half of the solution. This step declares which properties should be treated as secure, but it does nothing to actually hide the values if they are still being passed in as cleartext by the CI/CD pipeline. The question states the current process uses cleartext, so this option alone doesn't fix the problem.
Why C is Incorrect:
Adding parameters to the wrapper.conf file is a method for passing JVM arguments. This is not the standard or secure method for application-level properties in CloudHub. These values would likely still be exposed in logs, build scripts, and would not be manageable through the Runtime Manager UI, failing the "changeable by administrators" requirement.
Why D is Incorrect:
This option misinterprets the mechanism. CI/CD pipeline scripts (like those in Jenkins) do not have a native feature to "declare variables as hidden" in a way that impacts Runtime Manager's visibility. The pipeline's role is to deploy the application without the sensitive values. The "hiding" is achieved by using the Secure Properties feature of the Mule runtime and Runtime Manager, not by a function within the pipeline script itself.
Key Architecture Principle & Reference
This question tests your knowledge of MuleSoft's separation of concerns for configuration management and the specific use case for Secure Properties in CloudHub.
Reference:
The MuleSoft documentation on Application Configuration in CloudHub explicitly describes secure properties: "Secure properties are properties whose values are encrypted... You can define which properties are secure in the mule-artifact.json file. Once you set a property as secure and deploy the application, you can set its value in Runtime Manager, and it will be stored encrypted."
In summary: The correct procedure is:
Declare the property keys in the secureProperties array of the mule-artifact.json file.
Modify the CI/CD pipeline to not pass the cleartext values for these properties during deployment.
Have a Runtime Manager Administrator set the encrypted values directly in the UI post-deployment.
A manufacturing company plans to deploy Mule applications to its own Azure Kubernetes service infrastructure. The organization wants to make the Mule applications more available and robust by deploying each Mule application to an isolated Mule runtime in a Docker container while managing all the Mule applications from the MuleSoft-hosted control plane. What choice of runtime plane meets these organizational requirements?
A. CloudHub 2.0
B. Customer-hosted self-provisioned runtime plane
C. Anypoint Service Mesh
D. Anypoint Runtime Fabric
Explanation
The question outlines several key requirements that uniquely point to Runtime Fabric:
Deploy to its own Azure Kubernetes Service (AKS) infrastructure:
The organization wants to use its own existing Kubernetes cluster in Azure. This immediately rules out MuleSoft's fully managed PaaS (CloudHub).
Deploy each Mule application to an isolated Mule runtime in a Docker container:
This is the core deployment model of Runtime Fabric. It is a container orchestration layer that runs Mule applications as Docker containers on a Kubernetes cluster.
Manage all the Mule applications from the MuleSoft-hosted control plane:
This is the defining characteristic of Runtime Fabric. It allows you to manage applications deployed on your own infrastructure (in this case, AKS) from the same, familiar Anypoint Platform (the MuleSoft-hosted control plane) that you would use for CloudHub. You get the operational benefits of a managed control plane while maintaining control over the underlying infrastructure.
Why the Other Options are Incorrect:
A. CloudHub 2.0:
While CloudHub 2.0 also uses a container-based architecture, it is a fully MuleSoft-managed runtime plane. You do not deploy it to your own AKS cluster; you deploy it to the CloudHub 2.0 environment managed by MuleSoft. The organization's requirement to use "its own Azure Kubernetes service infrastructure" makes this incorrect.
B. Customer-hosted self-provisioned runtime plane:
This refers to the traditional model of manually installing Mule runtimes on virtual machines (VMs) or bare-metal servers. This model does not involve Docker containers or Kubernetes, and the management is typically more manual and disconnected, not providing the same level of deep integration with the Anypoint Platform control plane as Runtime Fabric.
C. Anypoint Service Mesh:
This is a technology for managing and securing north-south traffic (API traffic into and out of your network) for APIs deployed on VMs or Kubernetes. It is not a runtime plane for Mule applications. It is an add-on for API governance and traffic management that can work alongside Runtime Fabric or other runtime planes, but it does not itself host or run Mule application containers.
Key References
MuleSoft Documentation: Runtime Fabric
This documentation describes how Runtime Fabric enables you to deploy and manage Mule applications on your own Kubernetes infrastructure.
MuleSoft Documentation: Compare Deployment Options
This resource clearly contrasts the different runtime planes, highlighting that Runtime Fabric is for customer-managed Kubernetes infrastructure with a MuleSoft-managed control plane.
Concept: The "Managed Control Plane, Managed Infrastructure" model of Runtime Fabric.
In summary, Anypoint Runtime Fabric is the specific product designed to meet the exact requirement of running Mule applications in Docker containers on a customer-managed Kubernetes cluster (like AKS) while being managed from the central Anypoint Platform.
| Salesforce-MuleSoft-Platform-Integration-Architect Exam Questions - Home | Previous |
| Page 7 out of 55 Pages |