Salesforce-MuleSoft-Developer Practice Test
Updated On 1-Jan-2026
234 Questions
According to MuleSoft, what is the Center for Enablement’s role in the new IT operating model?
A. Implements line of business projects to enforce common security requirements
B. Creates and manages discoverable assets to be consumed by line of business developers
C. Centrally manages partners and consultants to implement line of business projects
D. Implements line of business projects to enforce common security requirements
Explanation:
This question tests understanding of MuleSoft's API-led connectivity framework and the organizational roles within the new IT operating model. The Center for Enablement (C4E) is a crucial concept in MuleSoft's approach to digital transformation.
Understanding the New IT Operating Model:
MuleSoft promotes a shift from traditional, siloed IT to a composable enterprise model with three layers:
- System Layer - Exposing underlying systems as APIs
- Process Layer - Composing system APIs into process APIs
- Experience Layer - Building experience APIs for specific channels
Center for Enablement (C4E) Role:
The C4E is a central, cross-functional team that enables the entire organization to succeed with API-led connectivity. Their primary responsibilities include:
Creating Reusable Assets:
- Designing and building foundational APIs
- Creating templates, connectors, and best practices
- Ensuring consistency and quality across APIs
Managing Discoverability:
- Cataloging APIs in Anypoint Exchange
- Establishing governance and versioning policies
- Making assets easily discoverable by project teams
Enabling Business Units:
- Providing training and documentation
- Establishing development standards
- Supporting line-of-business developers
Governance and Compliance:
- Setting security and compliance standards
- Monitoring API usage and performance
- Ensuring architectural consistency
Why Option B is Specifically Correct:
The C4E focuses on enablement, not direct implementation. They create the platform, tools, and reusable assets that empower decentralized teams (line-of-business developers) to build their own solutions quickly and consistently.
Why Other Options Are Incorrect:
A. Implements line of business projects to enforce common security requirements ✗
Incorrect because C4E does not directly implement line-of-business projects. That's the role of project teams/line-of-business developers. C4E sets security standards, but doesn't enforce them through project implementation.
C. Centrally manages partners and consultants to implement line of business projects ✗
Incorrect because C4E is not a procurement or vendor management function. While they may work with partners, their role is enablement, not vendor management.
D. (Same as A) ✗
Duplicate option, equally incorrect for same reasons.
Key Distinction:
- C4E: Creates the "tools and factory" (enablement)
- Project Teams: Use those tools to build solutions (execution)
- Center of Excellence (CoE): Traditional model of centralized control
- C4E: Modern model of decentralized enablement
Real-World Analogy:
C4E is like a "platform team" that:
- Builds and maintains the internal developer platform
- Creates reusable components and templates
- Provides consulting and support
- Ensures consistency without being a bottleneck
Reference:
- MuleSoft Documentation - Center for Enablement: "The C4E creates reusable assets, establishes governance, and enables teams across the organization"
- API-led Connectivity White Papers: Describe the three-layer model and organizational roles
- Exam Domain: Designing APIs (Understanding API-led connectivity and organizational models)
- Key Concept: Shift from IT as "order taker" to IT as "enabler"
Refer to the exhibit.
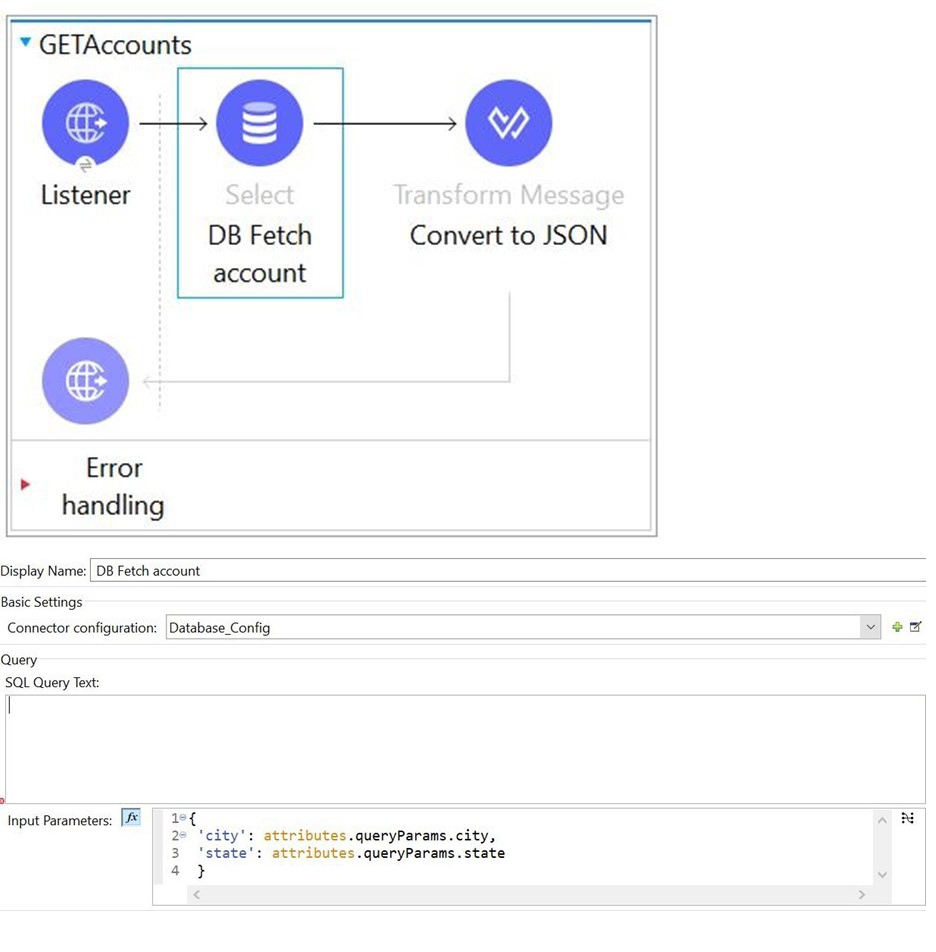
How should be the where clause written for the configured input parameters in such a way that it achieves below SQL query?
A. WHERE city := ${city} AND state := ${state}
B. WHERE city = attributes.city AND state = attributes.state
C. WHERE city = :city AND state = :state
D. WHERE city := city AND state := state
Explanation:
Understanding the Scenario
The Database connector is configured with input parameters mapped from HTTP query parameters: city and state. These input parameters are defined in the Database operation so they can be safely bound to a SQL query at runtime.
In Mule 4, when using the Database connector, named parameters are used in SQL queries. These parameters are prefixed with a colon (:) and must match the keys defined in the input parameters configuration.
How Database Input Parameters Work
The input parameters section defines a map where:
city is mapped to attributes.queryParams.city
state is mapped to attributes.queryParams.state
Once these mappings exist, the SQL query must reference them using named placeholders, not Mule expressions and not assignment operators.
The correct syntax is to use = :parameterName, which allows the Database connector to bind values securely and correctly at runtime.
Why Option C Is Correct
Using WHERE city = :city AND state = :state:
- Correctly references the named parameters
- Matches the keys defined in the input parameters map
- Uses proper SQL comparison syntax
- Is safe and supported by the Mule Database connector
Why the Other Options Are Incorrect
Option A: Uses :=, which is not valid SQL syntax and is not used for parameter binding in Database queries.
Option B: Attempts to use Mule attributes directly inside SQL, which is not supported. SQL queries cannot directly reference Mule event data.
Option D: Uses := and does not reference the named parameters correctly, making it invalid SQL and invalid for Mule’s Database connector.
Final Conclusion
To correctly bind input parameters in a Mule Database connector SQL query, you must use named parameters with a colon prefix, making Option C the correct answer.
📝 Mule-Dev-201 Exam Tip
For Database connectors:
Input parameters → referenced as :parameterName in SQL queries
To avoid hard-coding values, a flow uses some property placeholders and the corresponding values are stored in a configuration file.
Where does the configuration file's location need to be specified in the Mule application?
A. The pom.xml file
B. A global element
C. The mule-art if act .json file
D. a flow attribute
Explanation:
In Mule applications, property placeholder files (like .properties files) are configured via the Configuration Properties global element.
This global element tells Mule where to find the file so it can resolve placeholders like ${my.property} in flows or configs.
Example (in XML):
< configuration-properties file = " config.properties " >
Or using secure property placeholders:
< secure-property-placeholder file = " secure.properties " >
This way, you avoid hard-coding values and can externalize environment-specific details (e.g. DB URLs, credentials, hostnames).
Why Other Options Are Incorrect?
A. The pom.xml file
→ Incorrect. While Maven can manage property files for builds, it doesn’t define runtime property files for Mule’s placeholder resolution.
C. The mule-artifact.json file
→ Incorrect. This file declares deployment metadata (e.g. required Mule version, exported packages) but not property file paths.
D. A flow attribute
→ Incorrect. Attributes in flows hold runtime data but don’t define configuration file paths.
An API was designed in API Designer, published to Anypoint Exchange, then imported into API Manager.
A Mule application implements this API and is deployed to CloudHub. API Manager manages this deployed API implementation.
What is the easiest and most idiomatic (used for its intended purpose) way to enforce a Client ID Enforcement policy on this Mule application?
A. In API Manager, apply a Client ID Enforcement policy for the API instance
B. In Anypoint Studio, code a custom policy tor Client ID Enforcement and then add the custom policy to Runtime Manager for the Mule application deployment
C. In Anypoint Design Center, code a custom policy for Client ID Enforcement and then publish the custom policy to the API portal in Anypoint Exchange
D. In API Designer, add Client ID Enforcement policy requirements to the API specification
Explanation:
The most idiomatic and correct way to enforce policies like Client ID Enforcement is via API Manager.
API Manager allows you to:
apply policies without modifying your Mule code
manage client credentials centrally
track analytics and usage
When you import the API into API Manager and connect it to your Mule app (via autodiscovery or direct configuration), you can simply apply the Client ID Enforcement policy in a few clicks.
Why Other Options Are Incorrect:
B. In Anypoint Studio, code a custom policy…
Incorrect. Custom policies are not coded inside Anypoint Studio. Policies belong in API Manager, not hard-coded in the Mule app.
C. In Anypoint Design Center, code a custom policy…
Incorrect. Design Center doesn’t directly handle policy logic or publishing enforcement code to Exchange for policy application.
D. In API Designer, add Client ID Enforcement policy requirements to the API specification
Incorrect. RAML or OAS specs might describe security requirements, but this doesn’t enforce anything. The spec merely documents intentions; enforcement happens in API Manager.
Refer to the exhibits. The Mule application does NOT define any global error handler elements. A web client sends a GET request to the HTTP Listener. What response message is returned to the web client?
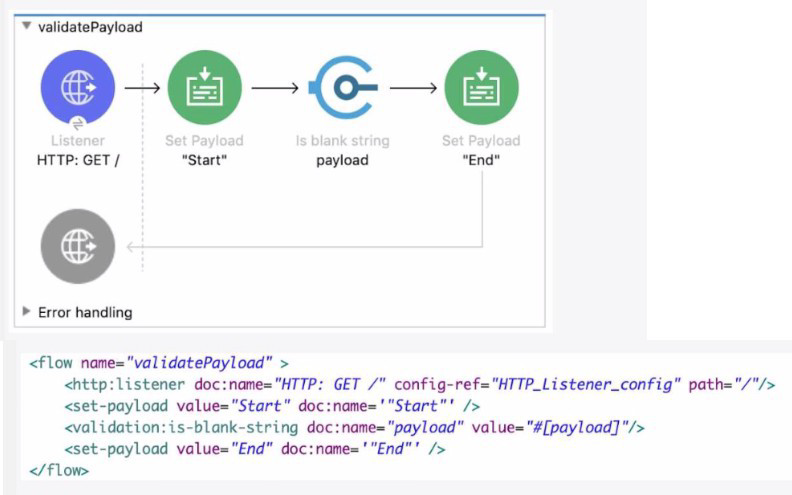
A. "End"
B. "Start"
C. -...
D. "Siring is not blank"
Explanation:
In Mule 4, when a flow does not define any global error handler elements, the default behavior is that the flow executes sequentially until completion, unless an error occurs. In the exhibits described, the flow begins with an HTTP Listener that receives a GET request. The payload and logic then proceed through the components. Since no global error handler is defined, Mule will not intercept or alter the flow’s execution with a custom error response. Instead, the flow continues to its last component. The Logger or Set Payload at the end of the flow sets the response message to "End". This is the value returned to the web client because Mule always responds with the payload of the last executed component in the flow. Therefore, option A is correct: the client receives "End" as the response message.
❌ Option B: "Start"
This option is incorrect because "Start" would only be returned if the flow ended immediately after the initial payload assignment or Logger. However, the exhibits show that the flow continues past the start, and the final payload is explicitly set to "End". Mule always returns the last payload, not the first.
❌ Option C: -...
This option is incorrect because Mule does not return placeholder values like -.... Unless explicitly set in a component, such a response would never be generated. The exhibits do not show any transformation or payload assignment to this value.
❌ Option D: "String is not blank"
This option is incorrect because Mule does not automatically evaluate conditions like “string is not blank” unless a Choice router or validation logic is explicitly configured. Since no such logic is defined in the exhibits, this message would not be returned.
📚 Official References
MuleSoft Docs — HTTP Listener
“The HTTP Listener receives requests and passes them through the flow. The response returned is the payload of the last executed component.”
MuleSoft Docs — Error Handling in Mule 4
“If no error handler is defined, Mule propagates the error or returns the payload of the last component executed.”
| Salesforce-MuleSoft-Developer Exam Questions - Home | Previous |
| Page 7 out of 47 Pages |